3 Minutes to Understand Dahua Product Security Whitepaper
With the maturity of AIoT technologies, responsible, open, professional, and systematic cybersecurity and privacy protection have become an important guarantee for the long-term and healthy development of the industry. As a world-leading video-centric AIoT solution and service provider, Dahua always attaches great importance to cybersecurity and privacy protection.
Recently, we released the Dahua Product Security White Paper 3.0 to help users and partners better understand the endogenous security protection capabilities of Dahua products, as well as our initiatives to comprehensively ensure security in R&D, compliance, emergency response and other areas.
PART 1 How do we guarantee the security and quality of full-range products?
We continue to promote the construction of secure Software Development Life Cycle (sSDLC). With security governance and risk management as the top-level guiding principle, and the security capability support platform as the base to facilitate the security control for each stage of the R&D process, including requirement, design, development, testing, and release, so as to ensure the security and quality of each delivered product.
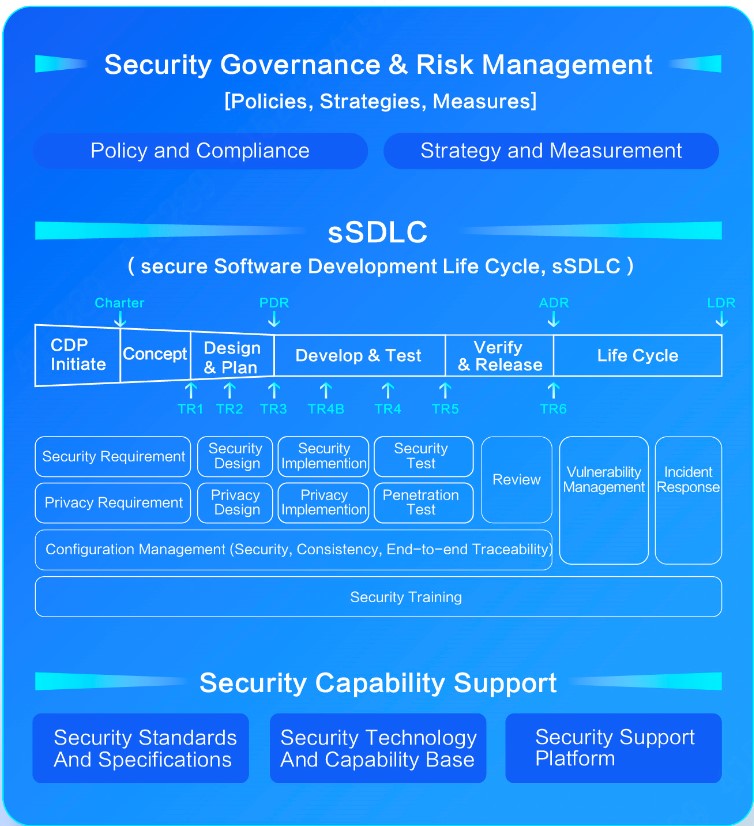
Dahua secure Software Development Life Cycle
We adopt a standardized, automated and digital process system to continuously improve the end-to-end management of security and privacy requirements, including security and privacy design, automatic detection of security coding, continuous integration of security testing, implementation of penetration testing and security assessment. At the same time, we carry out full-life cycle security training to enhance security and privacy awareness of employees, and comprehensively ensure that product security requirements are effectively implemented.
PART 2 How does our AIoT product security architecture work?
Dahua has built a security baseline and integrated a systematic endogenous security protection framework into its products to provide users with technical guarantees of default security. With the optimization and iteration of the security baseline, the product's built-in security protection framework will continue to be improved.
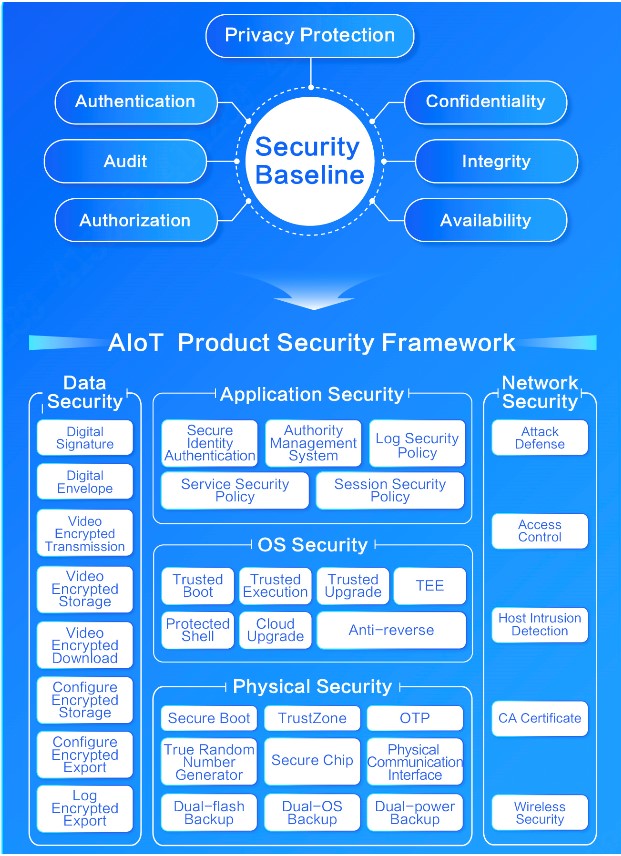
Dahua AIoT Product Security Framework
Based on the security and privacy design principles, we implement authentication, authorization, audit, confidentiality, integrity, availability and privacy protection as security elements for architecture design. At the same time, form a systematic AIoT product security framework that covers physical security, system security, application security, data security, network security, and privacy protection.

Dahua Product Security Center
The Dahua Product Security Center is designed to offer internal status self-inspection, external threat monitoring, real-time risk alert, in-depth protection management and other security features, assisting users better manage their devices. It acts as a security brain, assisting users to improve the protection capabilities of devices with convenient management experience.

AIoT Product Security Baseline
In order to ensure adequate and cutting-edge product security protection, we continue to focus on legal and regulatory compliance, standards and regulations learning, industry dynamic tracking, key technology research, security demand research and threat modeling analysis, etc. We continuously iterate security baseline standards to improve the security framework of AIoT products.
PART 3 How do we ensure product security and privacy compliance?
In the world of AIoT, where cyber threats loom large, Dahua stands firm in its dedication to global regulations and compliance standards that oversee network security, data integrity, and the cherished realm of privacy. Our robust security and privacy management approach, guided by mature security engineering expertise, weaves its protection throughout every phase of product creation, design, development, and distribution.
At the heart of our steadfast commitment, Dahua subjects its products to rigorous scrutiny, achieving a series of certifications that validate the integrity of our security measures and privacy protocols. These certifications include prestigious worldwide benchmarks like Common Criteria (CC), FIPS 140-2, ETSI EN 303645, etc. These exacting certifications bolster the core of our products, serving as an unwavering testament to reliability and an enduring pledge to unwavering privacy adherence.

PART 4 How we respond to product security incidents after delivery?
Based on the standardized vulnerability management process, Dahua provides 24/7 emergency response services for global users. We have a professional Product Security Incident Response Team (PSIRT) in place to receive, process and disclose any security vulnerability related to Dahua products and solutions.
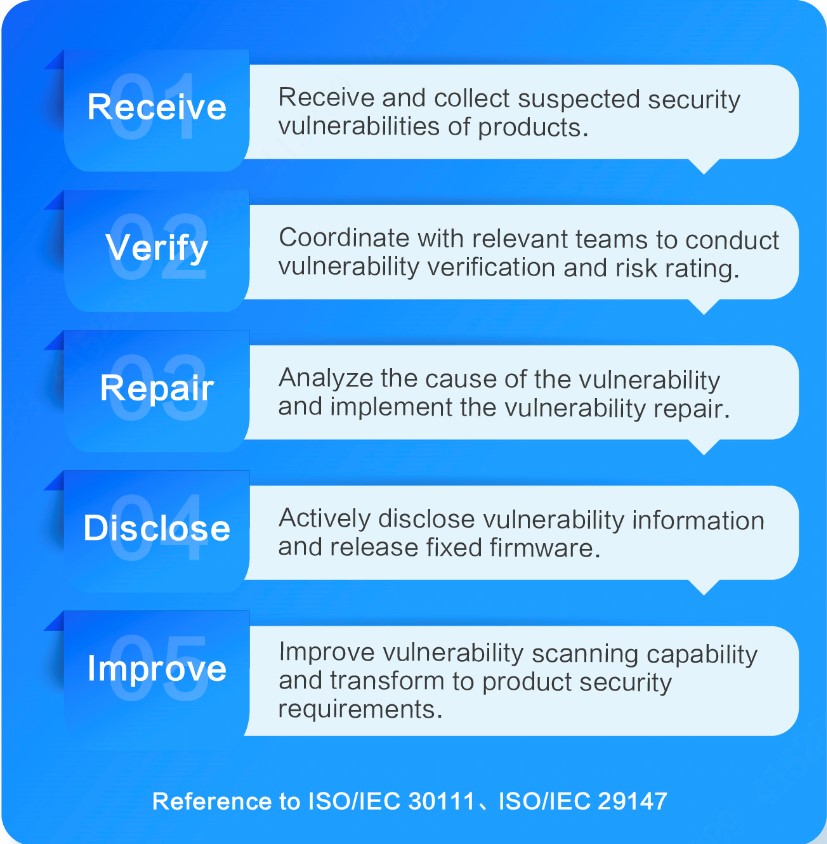
We communicate with industry organizations in an active and open manner, and have established a collaborative mechanism for mutual sharing. As a member of the international CVE Numbering Authority (CNAs), Dahua PSIRT implements a complete vulnerability management process in compliance with ISO/IEC 30111, ISO/IEC 29147 and other standards for transparent vulnerability reporting and handling.
We also encourage our partners, customers, and end users to conduct regular firmware updates and maintenance during the product life cycle and report to us any vulnerability discovered on any Dahua devices: psirt@dahuatech.com
Product security not only requires continuous efforts of manufacturers in R&D, production, delivery, etc., but also requires the active participation of users to improve the environment and methods of product use.
In the new journey of the AIoT era, Dahua will continue to consolidate its technical capabilities, focus on customer needs for actual scenarios, create business value for customers, and empower the digital-intelligent transformation of the industry. We are also committed to improving the environment and methods of product use through the joint responsibility and efforts of manufacturers, users, as well as other stakeholders to jointly ensure the secure operation of products.













